DORA & TLPT
Comprehensive audit services by Securitum

DORA
The Digital Operational Resilience Act (DORA) is an EU regulation that came into force on January 16, 2023, and will be applicable from January 17, 2025. The primary aim of DORA is to enhance the IT security of financial institutions such as banks, insurance companies, and investment firms, as well as their Information and Communication Technology (ICT) service providers. The regulation aims to ensure the operational resilience of these entities in the face of potential digital incidents.
Does DORA apply to my organization?
According to Article 2 of the DORA regulation, these provisions apply to financial institutions and financial service providers such as:
5 pillars of DORA regulation
Identifying and minimizing cyber threats through the implementation of risk management procedures within the organization.
Regularly conducting penetration tests in a live production environment, simulating real-world threats.
Implementing procedures for reporting, analyzing, and responding to digital incidents.
Assessing and monitoring risks related to service providers for financial sector institutions.
Ensuring the exchange of information between financial entities regarding current threats.
What is TLPT?
Threat-Led Penetration Testing (TLPT) is an advanced technical process designed to assess the cyber resilience of an organization against real-world threats. It involves Threat Intelligence reconnaissance, security testing of the IT environment in a live production setting (Red Team), and a final phase in which we collaborate with the client based on the findings from the tests.
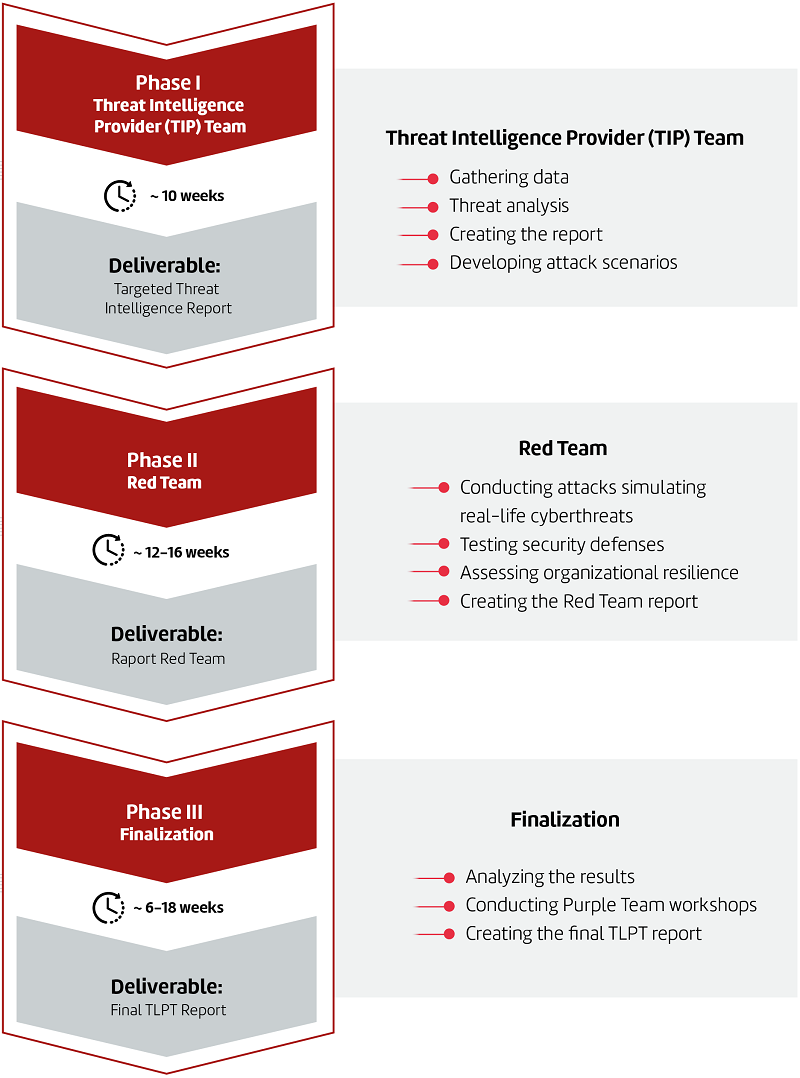
How we conduct TLPT tests
To ensure comprehensive execution of TLPT services in compliance with DORA regulations, Securitum works with two independent teams in three phases:
Phase 1 (approx. 10 weeks): Threat Intelligence Provider (TIP) Team
Deliverable: Targeted Threat Intelligence Report
In this phase, we gather intelligence and analyze open (OSINT) and closed (CSINT) sources of information to create a detailed report on targeted threats (Targeted Threat Intelligence Report). This report provides a comprehensive overview of the threat landscape, adversary profiles, attack methods, and potential attack vectors against the organization. Based on this analysis, the TIP team develops attack scenarios for use in the next testing phase.
Phase 2 (approx. 12-16 weeks): Red Team
Deliverable: Red Team Report
After completing the intelligence phase, we simulate real-world cyber-attacks based on previously created scenarios. Working within a live production environment, we test the security and resilience of systems, networks, procedures, and employee awareness. These simulated attacks are carried out discreetly to best replicate a potential breach attempt by adversaries and assess the organization’s resilience.
Phase 3 (approx. 6-18 weeks): Finalization
Deliverable: Final TLPT Report
In the final phase, we analyze the test results, develop reports, and collaborate with the cybersecurity team in Purple Team workshops. Based on the findings and the results of the workshops, we create a final TLPT report that summarizes the activities, security assessments of systems and procedures, and provides recommendations for improving security. This report is presented to the client and the regulatory authority overseeing the financial institution (TLPT Authority).
Risk management – additional ICT testing
One of the key requirements of DORA is effective risk management within the organization. The process of developing a risk management strategy should be based on reliable security assessments and the resilience of IT infrastructure. Securitum offers comprehensive audit services that allow for a thorough analysis of your company's IT environment, identifying potential gaps and vulnerabilities in systems. Our solutions ensure that your organization is properly prepared for any threats.
Web application penetration testing

Simulating attacks to identify vulnerabilities in web applications.
Infrastructure penetration testing

Testing network security to uncover weaknesses in servers and devices.
Cloud security assessment

Analyzing cloud systems to detect vulnerabilities and ensure proper data protection.
Social engineering

Simulating phishing attacks to evaluate employee awareness.
Mobile application penetration tests

Assessing mobile apps for security flaws.
SSDLC implementation

Incorporating security measures at every stage of software development.
Open Source Intelligence (OSINT)

Utilizing publicly available information to identify potential threats.
Desktop and console application

Identifying vulnerabilities in desktop software and implementing effective security measures.
Configuration analysis

Reviewing system settings to ensure compliance with best security practices.
Source code review

Analyzing code bases to detect errors and weaknesses, strengthening security.
Red teaming

Simulating real-world attacks to comprehensively assess the effectiveness of security measures.
Why Securitum?
Due to the high complexity of TLPT tests and the risks involved in conducting them in a live production environment, TLPT testing should only be carried out by top-tier experts. Securitum has been working with leading financial institutions in Poland and abroad for years, delivering the highest quality of services. Our team meets all the requirements outlined in Article 5 of the regulatory technical standards for TLPT testing.
As a leader in penetration testing in Central and Eastern Europe, Securitum conducts over 700 security tests annually. Our services are delivered by a team of 35+ cybersecurity experts whose credentials are validated by numerous certifications, publications, and reported CVEs. In the past three years, we have completed over 2,000 penetration tests, identified more than 10,000 vulnerabilities, and provided thousands of unique reports to hundreds of clients. We also conduct cybersecurity trainings and promote cybersecurity through our portal, sekurak.pl. We are the organizers of one of the largest cybersecurity conferences in Poland – Mega Sekurak Hacking Party – and the publishers of IT security books.
How to prepare for TLPT tests?
1. Understand DORA requirements
Start by familiarizing yourself with the regulations DORA imposes on your organization.
2. Conduct a preliminary security assessment
Identify key assets, systems, and procedures that should be tested in the audit.
4. Contact Securitum
Choose the best auditors in the market. Choose the best auditors in the market.
FAQ
Q:
What is the difference between TLPT and regular penetration testing?
While regular penetration tests focus on detecting common vulnerabilities in systems, TLPT tests are focused on simulating real-world threat scenarios that could be used by cybercriminal groups.
Q:
How often should TLPT tests be conducted?
According to DORA, TLPT tests should be conducted at least once every three years. However, it is recommended to perform them more frequently if there are significant changes or upgrades to IT systems.
Q:
In which language can the audit process be conducted?
The audit process can be carried out in either Polish or English, depending on the client's needs and preferences. The final report is also provided in the chosen language.
Q:
How long do TLPT tests take?
The duration of TLPT tests depends on the scope of the audit and the complexity of the system being tested, in agreement with the contracting organization and the supervisory body. According to DORA, the intelligence phase lasts approximately 10 weeks, and the Red Team phase lasts at least 12 weeks.


